
10 Aug 4 Crucial Steps You Should Take in Assessing Video Conference Security
4 Crucial Steps You Should Take in Assessing Video Conference Security
With remote work and video conferencing becoming more ingrained in the world’s workplace culture, we must ensure the applications and programs we use fit our security needs.
The Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency recommends that you take four actions while assessing the security of video conferencing applications.
These four actions include:
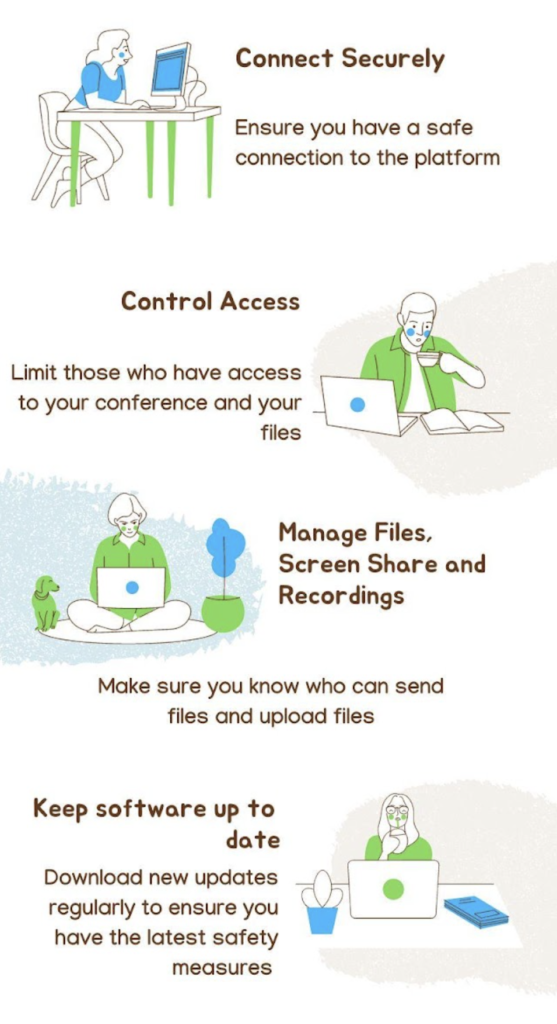
Connect Securely
Control Access
Manage Files, Screen sharing, and Recordings
Make sure your software is Up-to-Date
Connect Securely
It is important to make sure that you have a secure connection when video conferencing. Without secure access, people who should not have access to your information may get a hold of it. That is why it is crucial to look out for features that provide additional layers of security for all users. By having varied measures of security such as Two Factor Authentication (2FA) and encryption, you can rest assured that your connection and information is protected.
Research your industry compliance prior to using a platform.
Certain industries require additional compliances for performing their operations online.
Such examples can be seen in the accounting industry with its SOC-2 compliance and the medical industry with its mandatory HIPAA compliance. These measures are crucial in securing the data of clients.
Last but not least, whichever industry you belong to, if you work with sensitive data, make sure you ask if the platform is sharing any data with third parties. If they are, you might want to take a closer look at who your data is being shared with.
Control Access
It is important for you to have control over who can access your video conferences and shared files. Without the ability to control access, your files may be vulnerable. With Role-based Access, you can choose who can access what information in your organization. A good feature to look for is the ability to create meetings joinable by invitation only. This is a major security feature especially in the industries such as law or accounting. Last but not least, in video conferences, always look for the ability to create a waiting room and to remove members from the conference if needed.
Manage Files, Screen Share & Recordings
You should ensure that you have secure access to your files. Without securing your file access, you may have unwanted users uploading malicious content. One of the security measures you should look for when storing your files is Advanced Encryption Standard (AES) architecture. AES is a symmetric block cipher chosen by the U.S. government to protect classified information. It does so by transforming all your files into unreadable code, so it is close to impossible for any unauthorized users to access them.
An important feature for video conferencing is the ability to share your screen with your team or clients. When using such tools, make sure to look for applications that provide you the option to either select your whole screen or specific window so that no sensitive information is visible to participants.
Lastly, if a meeting recording is taking place during your video conference, as the meeting owner you need to make sure you have access to the recording so no sensitive information involving your meeting can be shared with unauthorized users.
Keep Your Software Up-to-Date
When using outdated video conference applications, there is a lot of risk involved. All the outdated applications are exposed with security flaws, which gives malicious hackers the ability to disrupt meetings’ privacy and access sensitive information.
One of the ways to ensure your software is up to date is to perform weekly update checks on the software you use. Another useful tool is to read patch notes to see which issues were fixed in the latest version. This way you can minimize the risk of running into bugs or security flaws.
If you would like to learn more about security measures or have any questions feel, free to schedule a free consultation or email us!
Contact:
Email: [email protected]
Phone Number: +1 (646) 970-2948




No Comments